A Licensed Cybersecurity Service Provider by Cybersecurity Services Regulation Office of Singapore
Organisations Of All Sizes Are At Risk From Hackers, Malware Threats And Ransomware Attacks. Endpoint Security Is The Cybersecurity's Frontline, And Represents One Of The First Places Organizations Look To Secure Their Enterprise Network. As The Volume And Sophistication Of Cybersecurity Threats Have Steadily Grown, So Has The Need For More Advanced Endpoint Security Solutions.

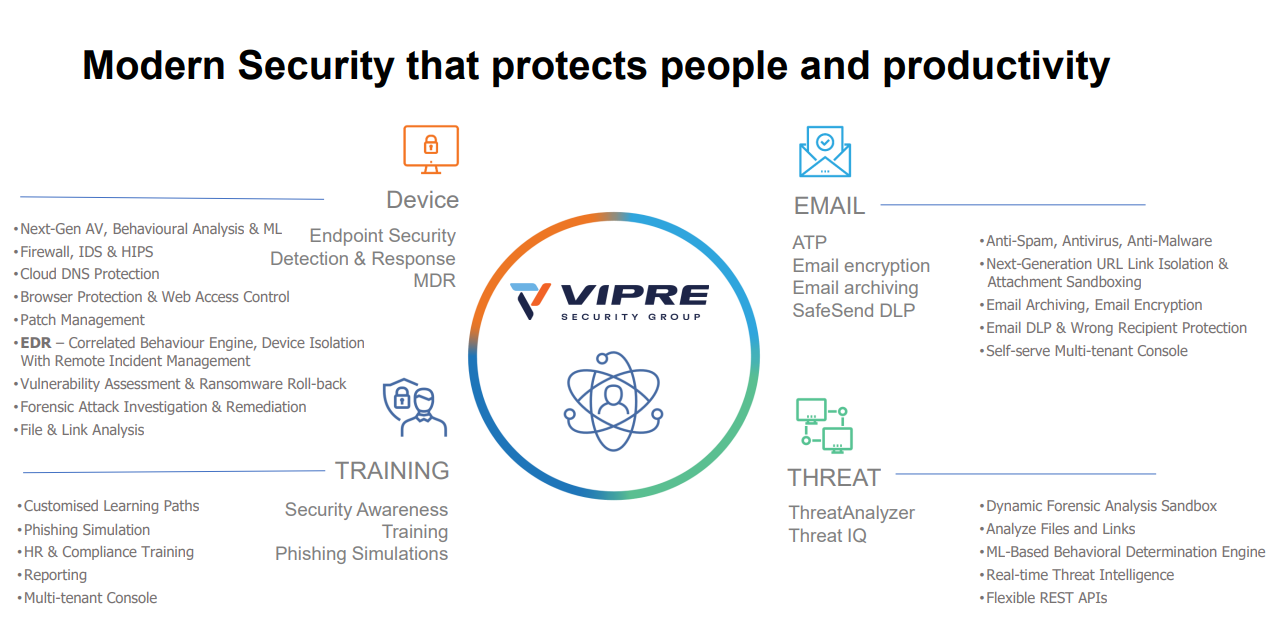
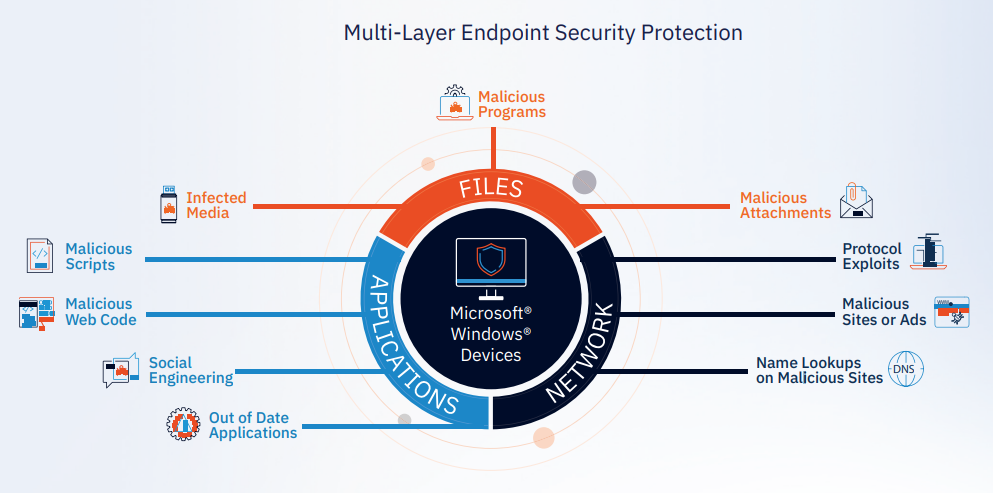
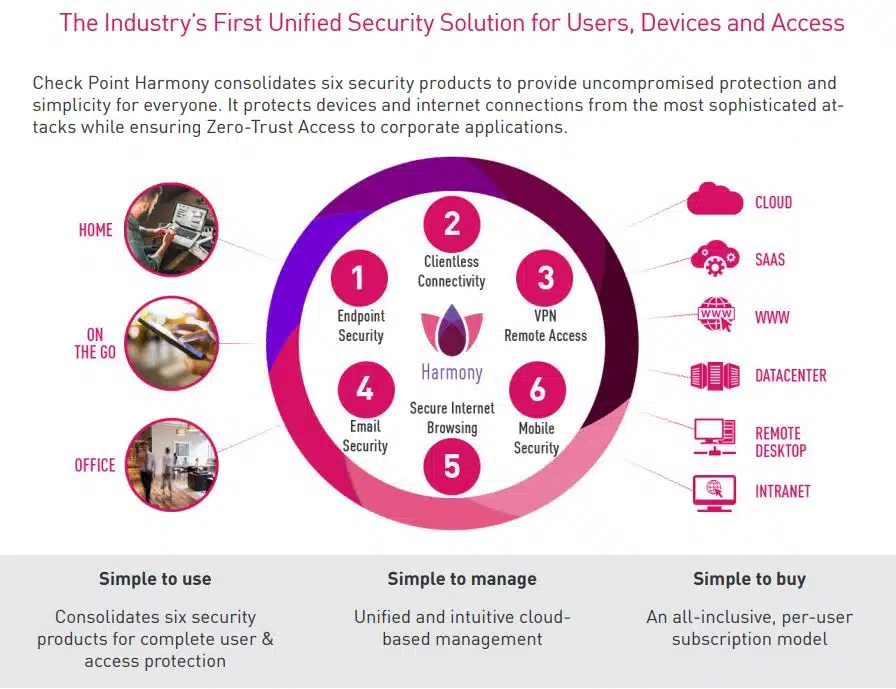
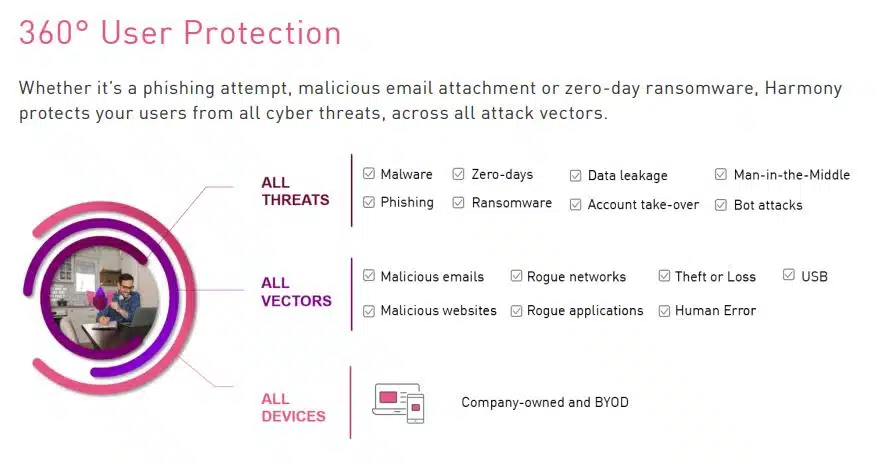
Compared to traditional security solutions, EDR provides enhanced visibility into your endpoints and allows for faster response time. Furthermore, EDR tools detect and protect organization from advanced forms of malware , APTs, phishing, etc.
EDR solutions are based on AI and machine learning algorithms designed to spot yet unknown types of malware, which will subsequently make behavior-based categorization decisions.
A wide range of data can be gathered from endpoints by using a software agent installed on each machine.
The data that was gathered from the endpoints are then sent to a centralized location.
Now that the data is collected, algorithms and machine learning technology are starting to sift through it in order to highlight potential irregularities.
It can be considered that many EDR solutions are able to “learn” what normal user behavior and endpoint operations are and make decisions based on this analysis.
The gathered data can also be correlated across multiple sources as threat intelligence feeds. These are used in order to provide real-world examples of ongoing cyberattacks that can be compared to the activity within an organization.
If the EDR views any events or actions as suspicious it generates an alert that the security analysts can easily review.
By using the automation capabilities that exist in EDR security solutions, the companies can actually have a faster response to a threat, as this type of solution is able to temporarily isolate an infected endpoint from the rest of the network in order to not allow malware to spread.


If you notice that some of your files have suddenly been encrypted without your knowledge, it could be a sign that your computer has been hacked. If the hacker demands money from you in exchange for decrypting these files, then you have a classic ransomware attack on your hands.
if you’re experiencing unusually slow internet speeds, it could be a sign that your network has been hacked. Hackers often use ‘stolen’ bandwidth to carry out their attacks and reduction in your connection speed could be a sign that you’re dealing with data breaches, external file transfers or malware.
One of the most common signs that you’ve been hacked is an increased number of complaints from your contacts or customers about unusually high email traffic from your account. This usually happens because the hacker has accessed your email account and is sending out spam or phishing emails from it. This is a common tactic used by hackers as they know that users are less likely to report spam emails if they come from a trusted email address..
If your passwords stop working, it may indicate that someone has hacked into your system and stolen your login credentials. This is a common tactic used by hackers, as it allows them to access your accounts unhindered and can be used to launch a ransomware attack.
If your browser settings are odd or the browser has new toolbars and plugins, it could open you up to malicious applications, websites and search redirection, which is what cybercriminals use to generate traffic and make money.
When annoying popup ads refuse to close or go away, it’s typically a bug and not a feature on a website.
Unwanted and unexpected software installs may appear on your system and are another common symptom of a cyber hack. Most modern malware programs are Trojans and worms and install along with legitimate programs.
Read software license agreements to determine if they’ll be installing more than one program. Opt out of other programs, if possible, or disable unrecognized programs after you check your installed programs.
Either you or someone else discovers your confidential data is up for sale on the internet or dark web. If you’re informed by a third party, you’ll need to verify that it’s true
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore.
Lorem, ipsum dolor sit amet consectetur adipisicing elit. Doloribus quam neque quibusdam corrupti aspernatur corporis alias nisi dolorum expedita veritatis voluptates minima sapiente.
Lorem ipsum dolor sit amet sed, consectetur adipiscing elit do obcaecati praesentium. Labore sint recusandae perspiciatis laudantium, deleniti non
Read More
Lorem ipsum dolor sit amet sed, consectetur adipiscing elit do obcaecati praesentium. Labore sint recusandae perspiciatis laudantium, deleniti non
Read More
Lorem ipsum dolor sit amet sed, consectetur adipiscing elit do obcaecati praesentium. Labore sint recusandae perspiciatis laudantium, deleniti non
Read More
Lorem ipsum dolor sit amet sed, consectetur adipiscing elit do obcaecati praesentium. Labore sint recusandae perspiciatis laudantium, deleniti non
Read More
Lorem ipsum dolor sit amet sed, consectetur adipiscing elit do obcaecati praesentium. Labore sint recusandae perspiciatis laudantium, deleniti non
Read More
Lorem ipsum dolor sit amet sed, consectetur adipiscing elit do obcaecati praesentium. Labore sint recusandae perspiciatis laudantium, deleniti non
Read More
Copyright © 2023 Syberhub. All Rights Reserved.